Nextcloud OIDC integration
Add lots of pictures
Document provider, application settings in Authentik
Document settings in Nextcloud
User quotas using custom attributes and property mappings
This commit is contained in:
parent
d5f0896cb4
commit
8479165a5d
pages/02.linux/authentik/nextcloud-oidc
Binary file not shown.
|
Before 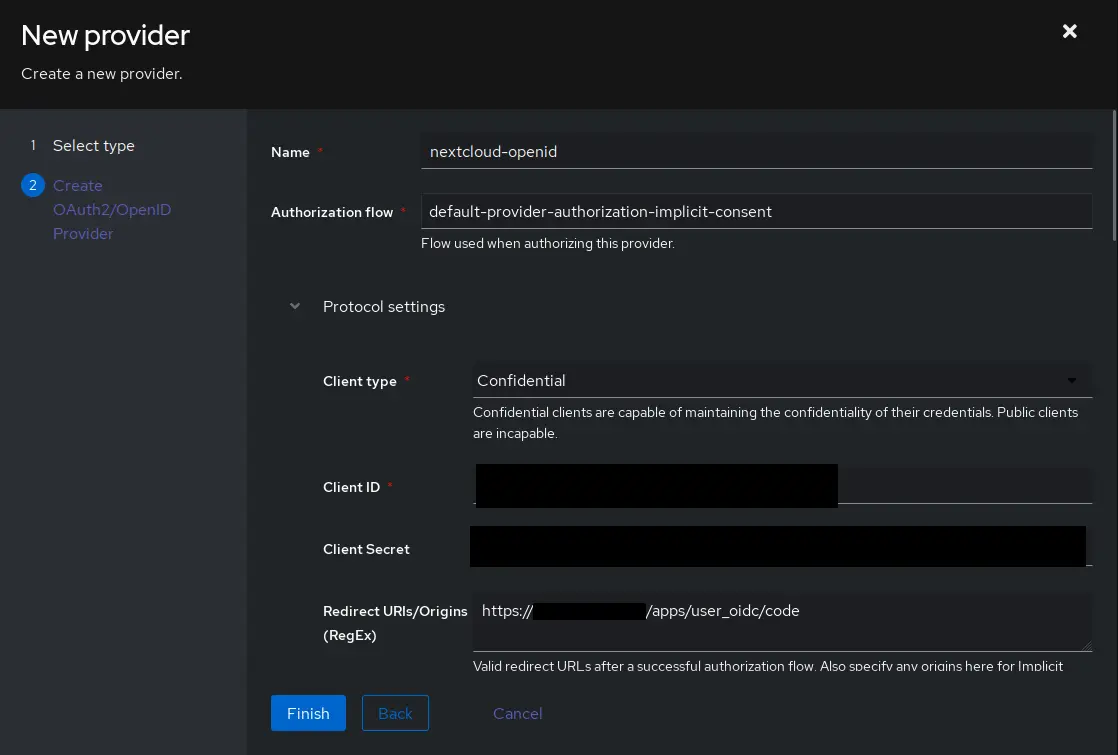
(image error) Size: 23 KiB After 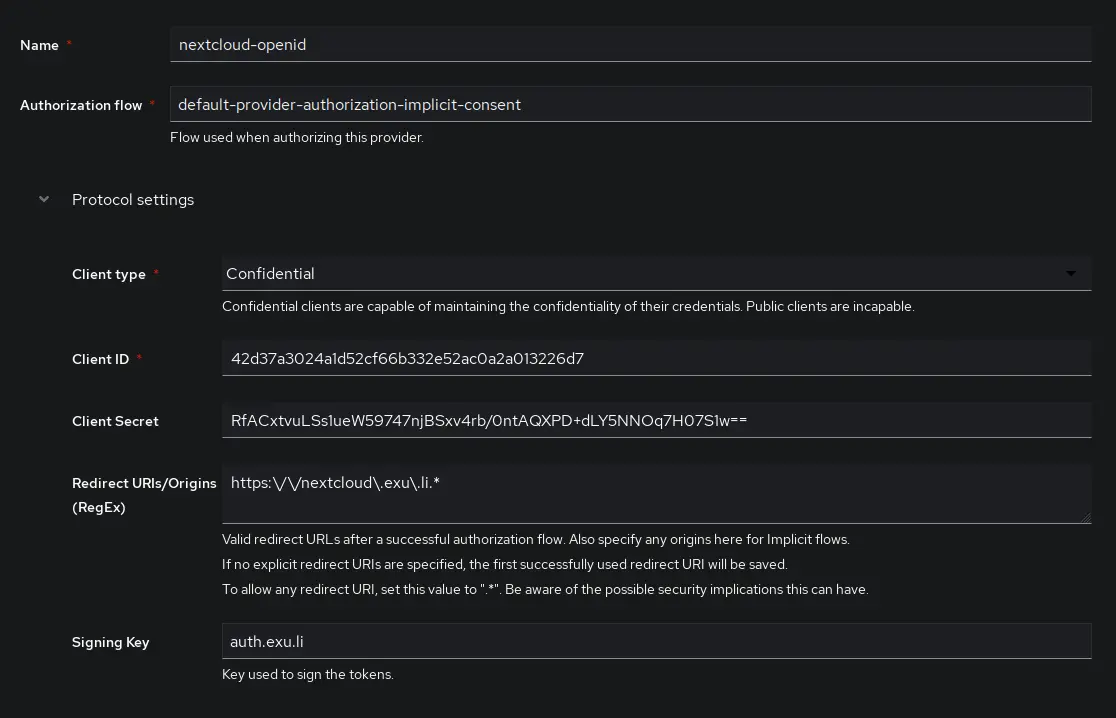
(image error) Size: 30 KiB 

|
Binary file not shown.
|
After 
(image error) Size: 13 KiB |
Binary file not shown.
|
After 
(image error) Size: 9.3 KiB |
@ -1,7 +1,7 @@
|
||||
---
|
||||
title: 'Nextcloud OIDC'
|
||||
title: "Nextcloud OIDC"
|
||||
visible: false
|
||||
media_order: 'authentik-create-provider.webp, authentik-create-application.webp'
|
||||
media_order: "authentik-create-provider.webp, authentik-create-application.webp, nextcloud-openid-connect.webp, authentik-custom-property-mapping.webp, authentik-oauth-scope.webp"
|
||||
---
|
||||
|
||||
[toc]
|
||||
@ -18,14 +18,14 @@ First, a new provider needs to be created. The setting can be found under `Appli
|
||||
|
||||
In the first screen, select `OAuth2/OpenID Provider` and click `Next`
|
||||
|
||||

|
||||
|
||||
- _Authorization flow_: default-provider-authorization-implicit-consent (Choosing explicit consent instead means the user has to approve every login)
|
||||
- _Client type_: Confidential
|
||||
- _Client ID_: The auto generated value is fine, copy it for use later.
|
||||
- _Client Secret_: **WARNING** user_oidc currently only supports values up to 64 characters in length. Make sure to trim the value below that, or generate a new secret with less characters. `openssl rand -base64 60` [Issue on user_oidc GitHub](https://github.com/nextcloud/user_oidc/issues/405)
|
||||
- _Redirect URIs/Origins_: https://{NEXTCLOUD URL}/apps/user_oidc/code
|
||||
- _Advanced protocol settings > Subject mode_: Based on the User's username, this setting should be used to ensure Nextcloud’s federated cloud ID will have a human-readable value
|
||||
- _Client Secret_: **WARNING** user_oidc currently only supports values up to 64 characters in length. Make sure to trim the value below that, or generate a new secret with less characters. `openssl rand -base64 40` [Issue on user_oidc GitHub](https://github.com/nextcloud/user_oidc/issues/405)
|
||||
- _Redirect URIs/Origins_: `https:\/\/nextcloud\.example\.com.*`
|
||||
- _Signing Key_: Set this to a valid TLS Certificate
|
||||
|
||||

|
||||
|
||||
### Create application
|
||||
|
||||
@ -36,4 +36,78 @@ Other settings can be left at their defaults.
|
||||
|
||||

|
||||
|
||||
Now, go back to the `Providers` screen and click on the previously created provider.
|
||||
Copy the value from `OpenID Configuration URL`, it should be something like `https://{AUTHENTIK URL}/application/o/{PROVIDER NAME}/.well-known/openid-configuration`
|
||||
|
||||
## Nextcloud
|
||||
|
||||
Log in as administrator, go to `Apps` and search for `OpenID Connect user backend`
|
||||
Click `Download and Enable` to install the app.
|
||||
|
||||
Next, open the administration settings in Nextcloud and go to `OpenID Connect`.
|
||||
Click on the `+` below `Registered Providers`
|
||||
|
||||
- _Identifier_: Authentik (This value is shown to the users when they try to log in)
|
||||
- _Client ID_: (value copied from Authentik)
|
||||
- _Client Secret_: (value copied from Authentik)
|
||||
- _Discovery endpoint_: (OpenID Configuration URL copied from Authentik, should end with .well-known/openid-configuration)
|
||||
|
||||
**Attribute mapping**
|
||||
|
||||
- _User ID mapping_: `sub`
|
||||
- _Display name mapping_: `nickname`
|
||||
|
||||
- Uncheck `Use unique user id`, otherwise nextcloud will hash the provided user id mapping together with the provider and use that as identifier. This is unnecessary unless you're using multiple providers with non-unique names.
|
||||
- Check `Use group provisioning` in order to create and update user groups in Nextcloud from Authentik.
|
||||
|
||||
All other settings here should be left at their default.
|
||||
|
||||

|
||||
|
||||
If you are running the Authentik in the same local network as Nextcloud and use internal addresses, you also need to add the setting `'allow_local_remote_servers' => true,` to your `config.php` file.
|
||||
Otherwise Nextcloud rejects the connection.
|
||||
|
||||
## Setting user quotas in Authentik
|
||||
|
||||
Using custom attributes, property mappings and scope mappings it is possible to set the desired storage quota for users.
|
||||
|
||||
### Assign custom attribute
|
||||
|
||||
Go to `Directory > Users`, click on a user and select `Edit`.
|
||||
In the field `Attributes` custom attributes can be specified in JSON or YAML format.
|
||||
|
||||
_Example_:
|
||||
|
||||
```yaml
|
||||
app-nextcloud-quota: 20G
|
||||
```
|
||||
|
||||
### Create propery mapping
|
||||
|
||||
Go to `Customisation > Property Mappings` and create a new mapping of the type `Scope Mapping`
|
||||
|
||||
The name can be chosen freely, choose something identifiable.
|
||||
Scope name will be used in the Nextcloud OpenID Connect config as scope.
|
||||
The expression is used to get the previously created custom attribute.
|
||||
|
||||
```py
|
||||
return {
|
||||
"quota": request.user.attributes.get("app-nextcloud-quota", "default"),
|
||||
}
|
||||
```
|
||||
|
||||

|
||||
|
||||
### Expose propery mapping
|
||||
|
||||
Click on the previously created provider for Nextcloud and select `Edit`.
|
||||
Go to `Advanced protocol settings > Scopes` and `CTRL + Click` the newly created Nextcloud quota mapping.
|
||||
|
||||

|
||||
|
||||
### Nextcloud config
|
||||
|
||||
Nextcloud needs to request access to the scope we just created.
|
||||
Simply add `quota` to the space separated list of Scopes in the OpenID Connect provider settings.
|
||||
|
||||
Changing the quota attribute, will update the storage quota for the user upon the next login.
|
||||
|
||||
Binary file not shown.
|
After 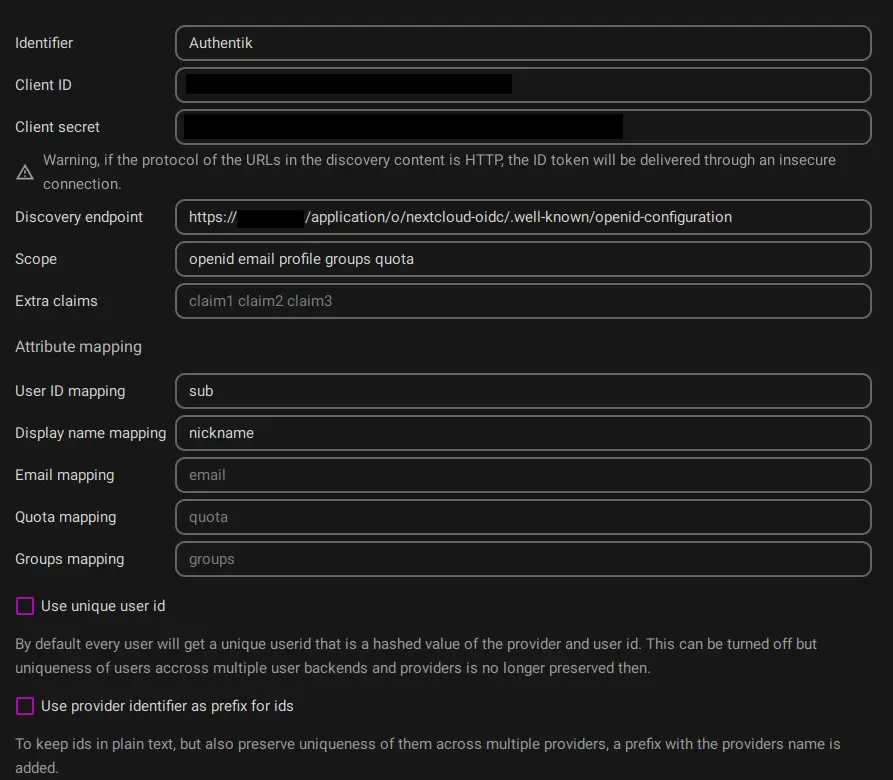
(image error) Size: 32 KiB |
Loading…
Reference in New Issue
Block a user